We’ve come a long way since the early days of OT security or should I say ICS security? Today there are several international bodies of standards and frameworks that focus on OT (Operational Technology) security.
It is common for organizations to develop their own unique set of policies, standards, and procedures tailored to their specific needs and objectives. While internationally accepted standards and frameworks can serve as valuable references and best practices, organizations often find it necessary to customize these standards to align with their internal processes, industry requirements, and organizational culture.
Let’s review the main OT Security standards and frameworks
- ISA99
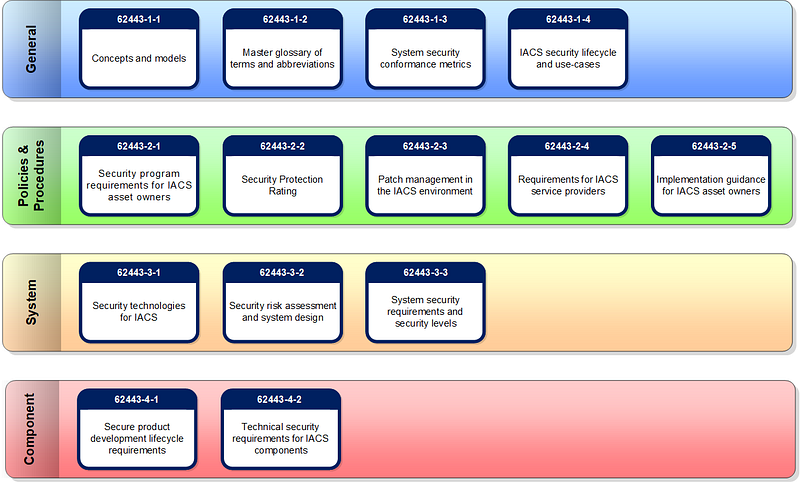
- ISA/IEC 62443
- NIST 800–82
- ISO/IEC 27001
- ENISA
- DHS CISA
ISA99
ISA99, which stands for International Society of Automation (ISA) Standard 99, is primarily a committee that publishes standards and recommendation for industrial automation systems which covers broad set of topics more than just security. You can see ISA99’s latest publications here.
ISA, initially known as the Instrument Society of America, originated on 28 April 1945 in Pittsburgh, Pennsylvania, USA. Richard Rimbach, the founder of the Instruments Publishing Company, conceived the idea, driven by the collective aspiration of 18 local instrument societies to establish a nationwide entity. Rimbach is acknowledged as the visionary behind the formation of ISA.
The ISA99 standards focus on defining a systematic approach to identifying, assessing, and mitigating cybersecurity risks in IACS. They provide guidelines for developing security policies, conducting risk assessments, implementing security controls, and managing the ongoing cybersecurity of industrial systems. ISA99 standards were the basis for the more internationally adopted standards of IEC 62443.
ISA99 Standards are the same price as the IEC 62443 at a few hundred dollars per document. To see the list of ISA99 standards click here and filter for “62443“.
ISA/IEC 62443
The International Society of Automation (ISA) collaborated with the IEC to develop the ISA/IEC 62443 series of standards. These standards address the cybersecurity of IACS, including concepts, terminology, and best practices for securing OT systems.
The IEC 62443 standards were initially introduced in 2010 and have undergone subsequent revisions to address evolving cybersecurity challenges.
Similar to ISA99, IEC 62443 standards provide a framework for establishing a robust cybersecurity program for IACS. They offer guidelines for identifying security vulnerabilities, implementing protective measures, conducting security assessments, and managing the security lifecycle of industrial systems.
NIST 800–82
The National Institute of Standards and Technology (NIST) in the United States has published Special Publication 800–82, titled “Guide to Industrial Control Systems (ICS) Security.” In 2006, recognizing the need for cybersecurity guidance in the industrial control systems domain, NIST released Special Publication (SP) 800–82 as a comprehensive resource to help organizations protect their ICS infrastructure. This initial publication focused on the security challenges specific to ICS and provided recommendations for securing these systems.
Over the years, NIST has periodically updated and revised the document to keep pace with evolving cyber threats and technological advancements. Each revision incorporates feedback from industry experts, stakeholders, and the cybersecurity community to ensure the guidelines remain relevant and effective.
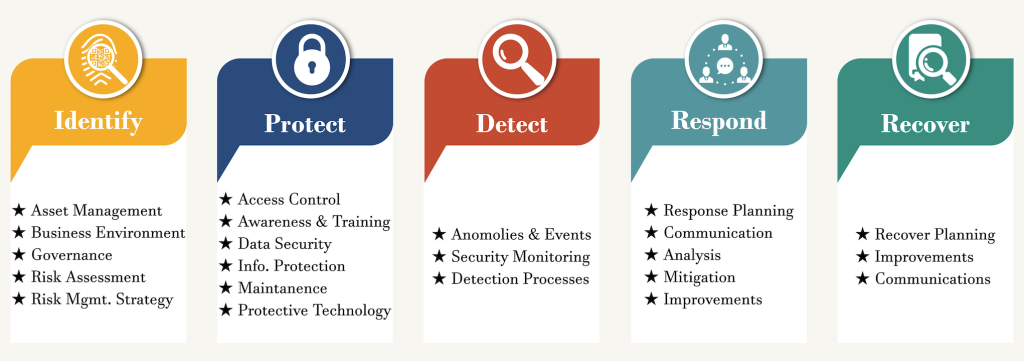
NIST framework categorizes all cybersecurity activities into five core functions:
- Identify: This function involves understanding and managing cybersecurity risks by identifying and documenting critical assets, vulnerabilities, and potential threats.
- Protect: The protect function focuses on implementing safeguards to ensure the security and resilience of critical systems and assets, including measures such as access controls, secure configurations, and training programs.
- Detect: This function emphasizes the ability to promptly and effectively identify cybersecurity events by establishing monitoring capabilities, conducting regular threat assessments, and implementing anomaly detection systems.
- Respond: The respond function involves developing and implementing response plans to address detected cybersecurity incidents, including mitigation actions, communication strategies, and coordination with external stakeholders.
- Recover: The recover function focuses on restoring operations and services following a cybersecurity incident, including activities such as system restoration, data recovery, and post-incident analysis to prevent future occurrences and improve resilience.
NIST 800-53
NIST SP 800-53, titled “Security and Privacy Controls for Federal Information Systems and Organizations,” provides a comprehensive set of controls and guidelines for securing federal information systems.
NERC CIP
The North American Electric Reliability Corporation (NERC) is responsible for establishing and enforcing reliability standards for the planning and operation of the North American bulk power system.
The Critical Infrastructure Protection (CIP) Standards compliance framework was developed in 2008 with the aim of addressing cybersecurity attacks on the Bulk Electric System (BES). Although these standards were initially voluntary, they were adopted as a means to mitigate risks and eventually became widely accepted as the industry standard.
NERC Critical Infrastructure Protection (CIP) plan consists of a set of standards specifically focused on the cybersecurity aspects of the Bulk Electric System. The NERC CIP standards aim to regulate, enforce, monitor, and manage the security of the BESs in North America.
| Standard | Topic |
| CIP-001 | Sabotage Reporting (Retired) |
| CIP-002 | Asset Identification and Classification Facility Classification Asset Identification Inventory Approval |
| CIP-003 | Policy and Governance Designation of Senior Responsible Official Policy Creation and Maintenance Policy Creation and Maintenance for Low-Impact Assets |
| CIP-004 | Personnel and Training Security Awareness Background ChecksTraining Access Management Access Review |
| CIP-005 | Network Security Creation of Electronic Security Perimeters or Virtualized Equivalents Management of Secure Interactive Remote Access |
| CIP-006 | Physical Security of Cyber Assets Physical Security Plans Creation and Monitoring of Physical Security Perimeters |
| CIP-007 | System Security Controls Patch Management Management of Ports and ServicesMalware Prevention Security Event Logging Management of Shared Accounts Password and Credential Management |
| CIP-008 | Cyber Security Incident Response |
| CIP-009 | Recovery Plans Continuity of Operations Backup and Restoration |
| CIP-010 | Change and Vulnerability Management Configuration Capture and Management Change Management and Monitoring Vulnerability Management Management of Transient Cyber Assets |
| CIP-011 | Protection of BES Cyber System Information Classification and Protection of Information Disposal of Media |
| CIP-012 | Control Center Communications |
| CIP-013 | Supply Chain Security |
| CIP-014 | Physical Security of Key Substations |
DHS CISA
CISA, which stands for the Cybersecurity and Infrastructure Security Agency is under the U.S. Department of Homeland Security (DHS). It is the operational lead for federal cybersecurity efforts in the United States. It serves as the national coordinator for critical infrastructure security and resilience as well. CISA’s primary objective is to enhance the security and resilience of the nation’s critical infrastructure from both cyber and physical threats.
While not an international body of standard, CISA provides guidelines, resources, and frameworks for securing critical infrastructure, including OT systems. They offer a range of publications and tools to enhance the cybersecurity of OT environments. Their mission revolves around a layered approach to reduce risk to the nation’s cyber and physical infrastructure.
- Cybersecurity: CISA works to protect federal government networks, systems, and data from cyber threats. It provides cybersecurity tools, incident response assistance, and best practices guidance to federal agencies and other partners. CISA also engages in threat analysis and information sharing to help identify and mitigate cyber risks across the country.
- Infrastructure Protection: CISA collaborates with critical infrastructure owners and operators to identify and prioritize risks, develop protective measures, and enhance the resilience of vital systems. It supports the implementation of security measures and offers training and exercises to improve preparedness and response capabilities.
- Emergency Communications: CISA plays a critical role in ensuring the availability and reliability of communication systems during emergencies and crises. It works to maintain and enhance the nation’s emergency communications infrastructure, including systems used by first responders and government agencies.
- Risk Management: CISA promotes risk management strategies and provides resources to organizations to assess and mitigate risks to their critical infrastructure. This includes conducting vulnerability assessments, developing risk mitigation plans, and assisting with incident response and recovery efforts.
- Information Sharing: CISA facilitates the exchange of information and intelligence related to cybersecurity and infrastructure protection among various stakeholders. It operates several programs and platforms to disseminate timely and actionable information, enabling partners to stay informed about emerging threats and vulnerabilities.
CISA also has some of the best free OT Security training material. They offer an instructor lead training that is a one-week in-person training. Their website also has great content available on demand. Access the CISA VCISA Learning Portal for more information and to register for and complete the courses. There are no tuition costs for these courses.
ENISA
ENISA, the European Union Agency for Cybersecurity collaborates closely with EU Member States and various stakeholders to provide reports, advice, solutions, and support in the field of cybersecurity including for critical infrastructures . The agency’s primary objectives include improving cybersecurity readiness, fostering cooperation during cross-border incidents, and developing cybersecurity certification schemes.
As of 2019, the last year for which budget information is available on their website, ENISA had a budget of nearly €17 million. The agency also employed 70 statutory staff members. Additionally, it engaged other personnel, such as seconded national experts, trainees, and interim agents, to fulfill its responsibilities.
ENISA’s establishment traces back to Regulation (EC) No 460/2004, which was adopted by the European Parliament and the Council on March 10, 2004. This regulation formed the European Network and Information Security Agency (ENISA) with the aim of addressing network and information security challenges within the EU.
ENISA’s mandate has been extended and modified over the years through subsequent regulations. Regulation (EC) No 1007/2008, passed on September 24, 2008, amended the original regulation concerning the duration of ENISA’s mandate. Another modification came with Regulation 580/2011, approved on June 8, 2011, which further adjusted the duration of the agency’s mandate.
The most recent extension of ENISA’s mandate, before it became permanent, was accomplished through Regulation (EU) No 526/2013. This regulation, adopted on May 21, 2013, repealed the earlier Regulation (EC) No 460/2004 and provided an updated framework for ENISA’s operations.
MITRE ATT&CK ICS Framework
The MITRE ATT&CK ICS (Industrial Control Systems) framework is an extension of the MITRE ATT&CK framework that focuses on the unique cybersecurity challenges faced by industrial control systems. Industrial control systems are used in sectors such as energy, manufacturing, transportation, and utilities to control and monitor critical infrastructure.
The ATT&CK ICS framework provides a structured and standardized knowledge base of adversary tactics, techniques, and procedures (TTPs) specifically tailored to ICS environments. It helps organizations understand and analyze the potential attack vectors and tactics that adversaries might employ when targeting industrial control systems.
The framework consists of three main components:
- Tactics: The tactics represent the goals or objectives that adversaries aim to achieve when targeting ICS environments. Examples of tactics include Initial Access, Execution, Persistence, Lateral Movement, and Impact.
- Techniques: The techniques are the specific methods or actions used by adversaries to accomplish their objectives within the ICS environment. Each technique is associated with one or more tactics. Examples of techniques include Exploit Public-Facing Application, Remote File Copy, Command and Control, and Data Destruction.
- Procedures: The procedures describe the step-by-step sequences of actions that adversaries follow to execute specific techniques. These procedures provide more detailed insights into how adversaries might carry out attacks against ICS systems.
ISO/IEC 27001
While not specific to OT security, ISO/IEC 27001 is an international standard for information security management systems (ISMS). It provides a framework for establishing, implementing, maintaining, and continuously improving an organization’s information security management.